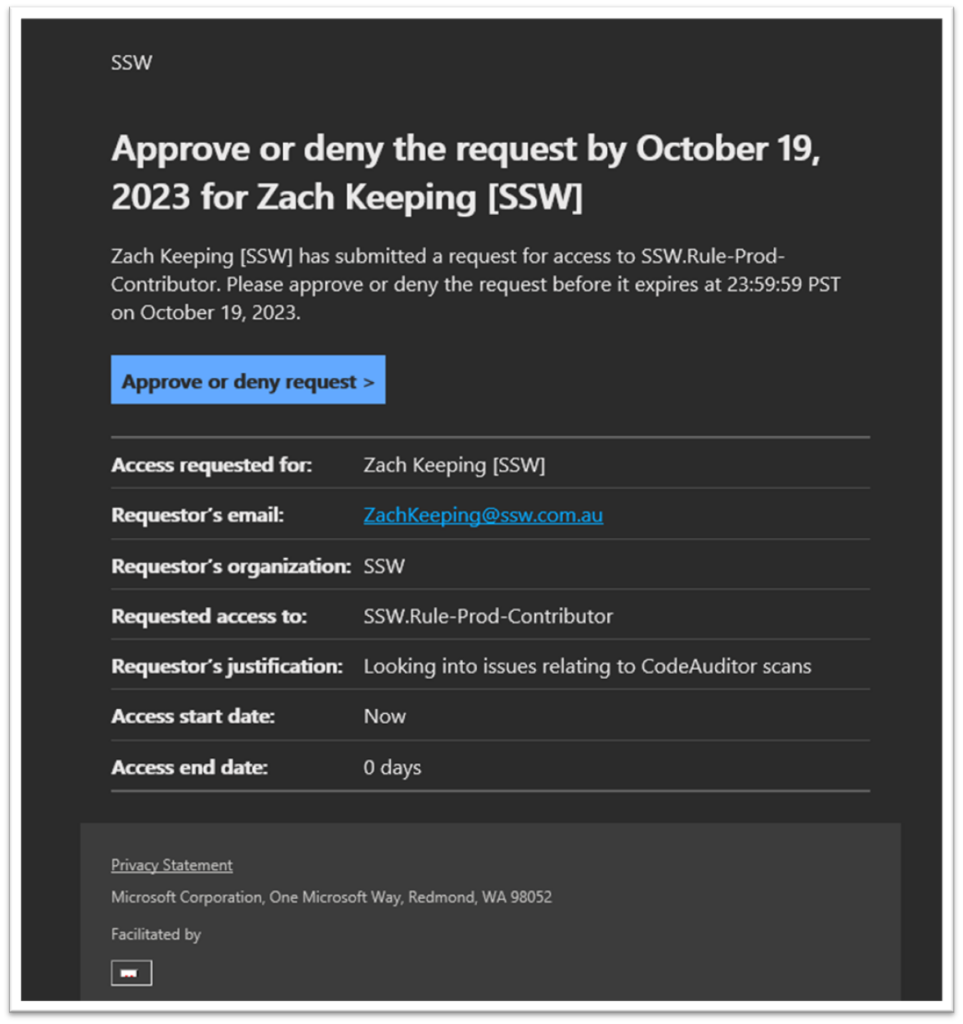
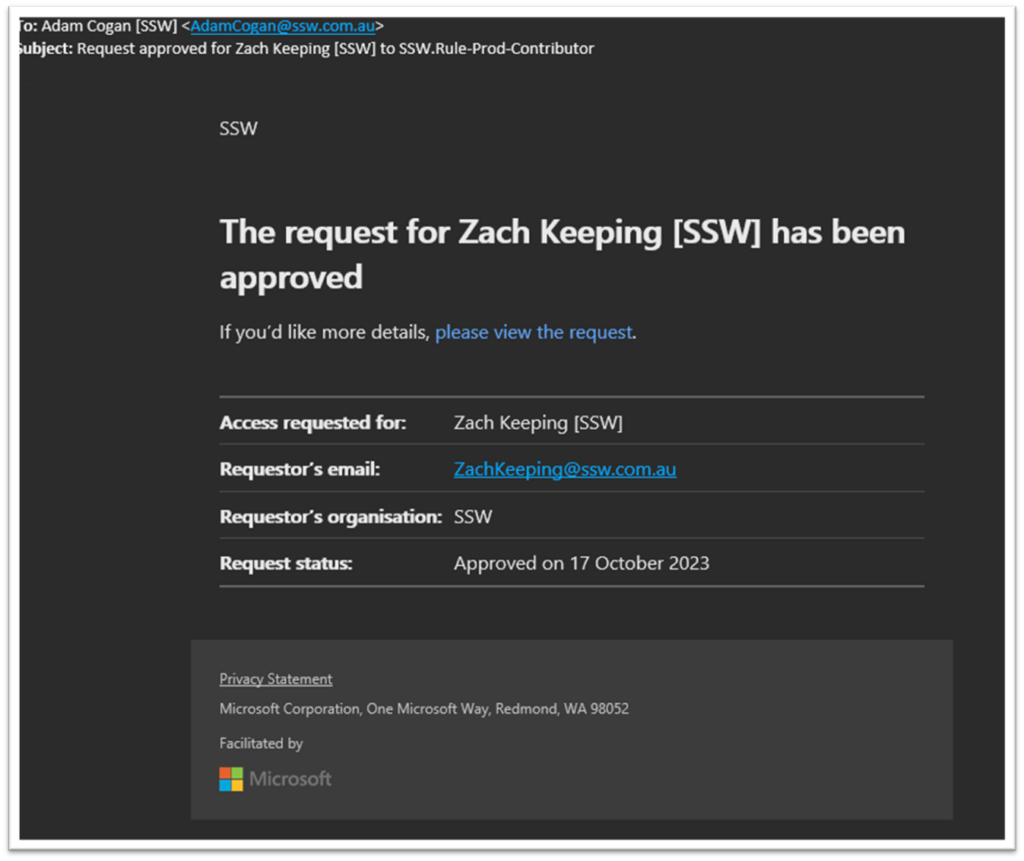
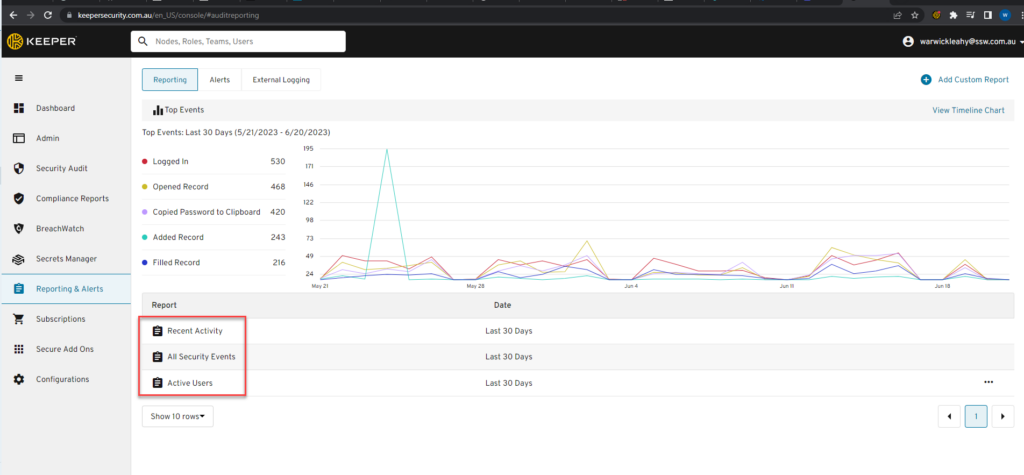
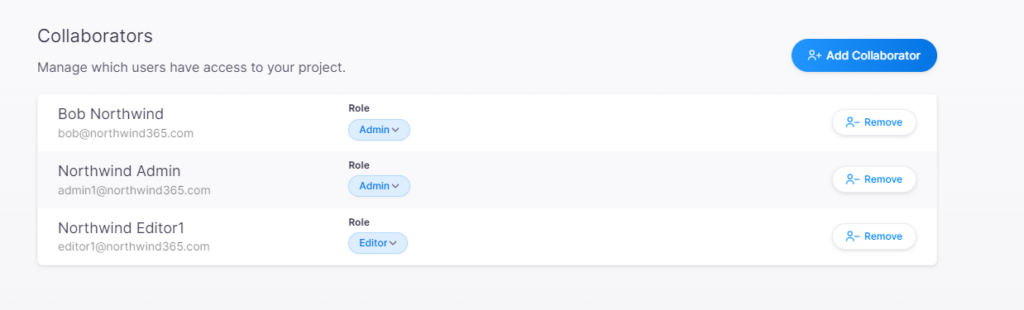
OIDC is the recommendation method to login to Azure from GitHub pipelines now as it provides better security and doesn’t rely on storing a secret.
Currently OIDC login tokens expire in just 5 minutes🔥, causing long running scripts to fail.
Related GitHub Issue: https://github.com/Azure/login/issues/180.
Your Azure credentials have not been set up or have expired,
1955 | please run Connect-AzAccount to set up your Azure credentials.
1956 | ClientAssertionCredential authentication failed: A
1957 | configuration issue is preventing authentication - check the
1958 | error message from the server for details. You can modify the
1959 | configuration in the application registration portal. See
1960 | https://aka.ms/msal-net-invalid-client for details. Original
1961 | exception: AADSTS700024: Client assertion is not within its
1962 | valid time range. Current time: 2022-10-20T07:47:12.7446078Z,
1963 | assertion valid from 2022-10-20T07:37:08.0000000Z, expiry time
1964 | of assertion 2022-10-20T07:42:08.0000000Z. Review the
1965 | documentation at
❌ Bad example – Error on deployment – assertion valid from 2022-10-20 07:37 to 2022-10-20 07:42 🔥(5 minutes)
- uses: azure/login@v1
with:
client-id: ${{ env.CLIENT_ID }}
tenant-id: ${{ env.TENANT_ID }}
subscription-id: ${{ env.SUBSCRIPTION_ID }}
enable-AzPSSession: true
❌ Bad example – Needs 1 more parameter – (e.g. token-expiry: 30M)
- uses: azure/login@v1
with:
client-id: ${{ env.CLIENT_ID }}
tenant-id: ${{ env.TENANT_ID }}
subscription-id: ${{ env.SUBSCRIPTION_ID }}
enable-AzPSSession: true
token-expiry: 30M
✅ Good example – Allow the token expiry to be set to a more reasonable time
 -
-